As part of the Systems Security course, myself and another student (Aðalsteinn) performed a security investigation on a mobile application called ‘Flytoget’. The application allows users to purchase and view train tickets to and from Oslo airport. By leveraging techniques we learned throughout the course, we were able ascertain weak security implementations of the applcation, resulting in a number of vulnerabilities being uncovered, including account takeover. The process was very revealing as to the realities of security in widely used applications that handle sensitive data. Let’s take a quick look at one of the vulnerabilities discovered and explain how good secuirty pracitce could have prevented it.
The authentication mechanism is roughly shown as follows:
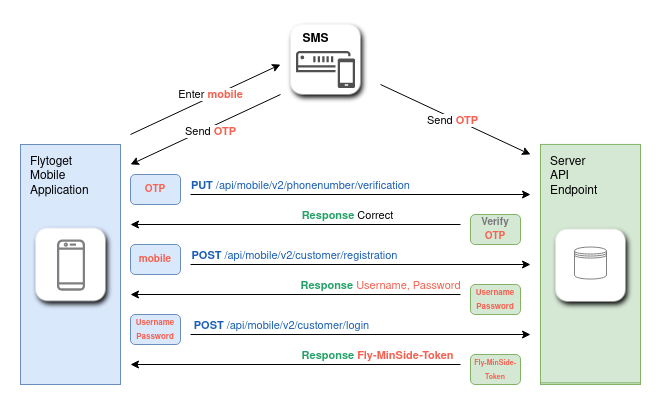
Through inspecting the authentication workflow, we uncovered that the OTP in no way binds the app to login to a specific user. We observed in the request headers for /registration that there were no tokens or auth cookies to verify the request. This enabled us to send requests with a modified phoneNumber. If an account exists for the phone number, a valid userName and password is returned.
Hence, we could perform a malicious attack as follows:
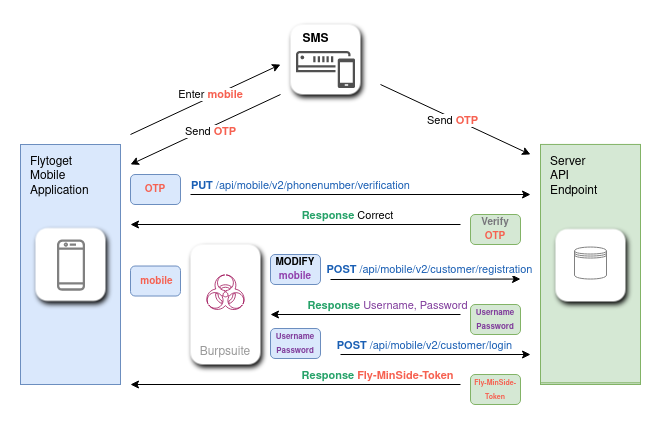
Through the help of our professor, Diego, we contacted the company to disclose the vulnerabilities. They were grateful for the report, and have said that the vulnerabilities have been fixed. We have not performed a review of claimed fixes. The company have not put out a disclosure statement regarding potential leaking of confidential user data. We only exploited our own accounts for obvious reasons.